IPv6
Tim's IPv6 Firewall Tester (IPv6 TCP/IP Port Scanner)
Introduction
Recent web-browsers request IPv6 DNS lookups in preference to IPv4 if they are running on a host with IPv6 enabled. My domain (ipv6.chappell-family.com) has DNS entries for both IPv4 and IPv6 addresses, but defaults to IPv4. This makes it safe for IPv4-only hosts, which make up most of the current web traffic, including search engines, to use the same URL. Browsers running on IPv4-only hosts will not request an IPv6 address and will therefore access the website entirely using IPv4. The landing page, as linked below, attempts to determine whether your machine has a valid globally routable IPv6 address (2000::/3) and whether it is behind an HTTP proxy, by looking for well known HTTP header variables which indicate that this may be the case. Only if the hosts' IP address is determined to be globally routable unicast IPv6 and there are no tell-tale HTTP proxy variables will the landing page offer links to initiate the scan.
The Test
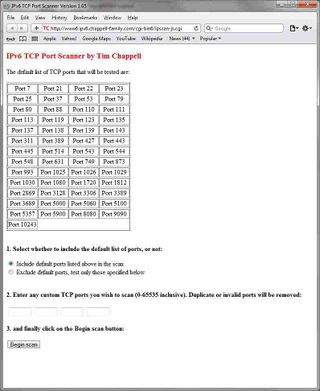
The tester allows a user to choose whether to include a commonly used set of IPv6_Ports in their scan, as well as the ability to specify a number of their own specifically interesting ports (this is intended to cover setups where you run services on non IANA-assigned ports, or just run less-common services). If you would like to see the list of commonly used ports expanded, or just changed, then please contact me.
The test begins by sending an ICMPv6 ECHO-REQUEST (an IPv6 ping) towards the host under test (HUT). The tester checks for related ICMPv6 responses from either the HUT or other hosts (e.g. routers and/or firewall devices protecting the HUT). If a response is detected from an host other than the HUT then the IPv6 address of this third-party is reported.
The test continues by scanning the user-selected IPv6 TCP/IP ports. The test sets its' socket tx/rx timeouts to be 1 second - consequently the results can take up to 1s per tested port - although this depends heavily upon the filtering your system employs (e.g. firewalls which mark protected ports as 'administratively prohibited' will resolve as PHBTD in much less than the allowed 1 second timeout assuming that your firewall sends an ICMPv6 type 1 code 1 packet in response).
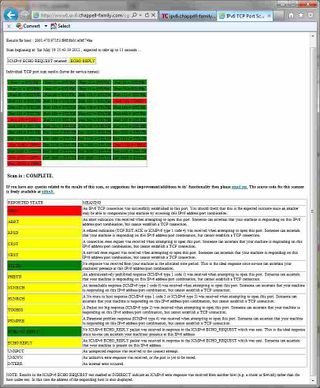
The tester will indicate the status of the tested ports as either OPEN, STEALTHed or one of a series of other states depending on the positive or negative feedback received from your machine. For a more detailed explanation of the reported states please read ScanStatus.
The tester is made available in two versions - one for browsers supporting javascript and the other suitable for text-only browsers such as Lynx and w3m. The text-only browser version can be used on hosts which do not sport their own GUI environment (e.g. servers). The javascript browser version supports ongoing updates of the test status, whereas the text-only version only produces a results page once all the selected ports have been tested.
IMPORTANT: this scanner will direct IPv6 TCP and ICMPv6 traffic towards the IP address that my webserver determines the request originates from. Please do NOT attempt to test machines that are operating behind HTTP proxies, unless you also administer the proxy and specifically intend that machine to be tested.
If you wish to test your host then please point your browser towards my IPv6 portscanner to test your clients' IPv6 firewall.
Automation
If you'd like to automate testing, or run the same test a number of times on different hosts then please see my ScanAutomation section.
Issues
If you're having trouble accessing the landing page via IPv6 then please see the following IPv6_DEBUG section.
Screenshots of a typical test
Below are screenshots taken from an example session - showing the landing page, test kickoff page and results page:
Getting an IPv6 connection
If you don't already have an IPv6 connection but wish to get involved, then try a tunnel broker such as Hurricane Electric or SixXS.
Source code
If you would like to view or use the scanner source code then please visit github.
<adsense>1</adsense>